
Phishing is a prevalent form of online fraud where cybercriminals attempt to trick victims into revealing sensitive information. As the name implies, these scammers are fishing for information, be it credit card numbers, bank account details, or social security numbers. And, unfortunately, they’re common and highly effective.
In 2023, nearly 300,000 Americans reported being victimized by phishing attempts. According to AAG, victims lose, on average, $136 per attack, leading to a countrywide loss in the tens of millions of dollars annually.
Below, we’re going to break down real-world examples of phishing scams across various channels, equipping you with the knowledge to identify and avoid these threats.
Example 1: Phishing Emails
Email accounts are the most common entry points for cyberattacks. In fact, more than 90% of successful cyberattacks begin with a phishing email. Emails can be easily mass-distributed and appear to come from legitimate sources. They’re so pervasive that over 80% of respondents said their organization was infiltrated in 2021 by a cyberattack initiated by a phishing email.
Let’s take a look at a phishing example below and how to know for certain that it’s a scam.
Note: WatchStreaming is not a real company and is being used only as an example.
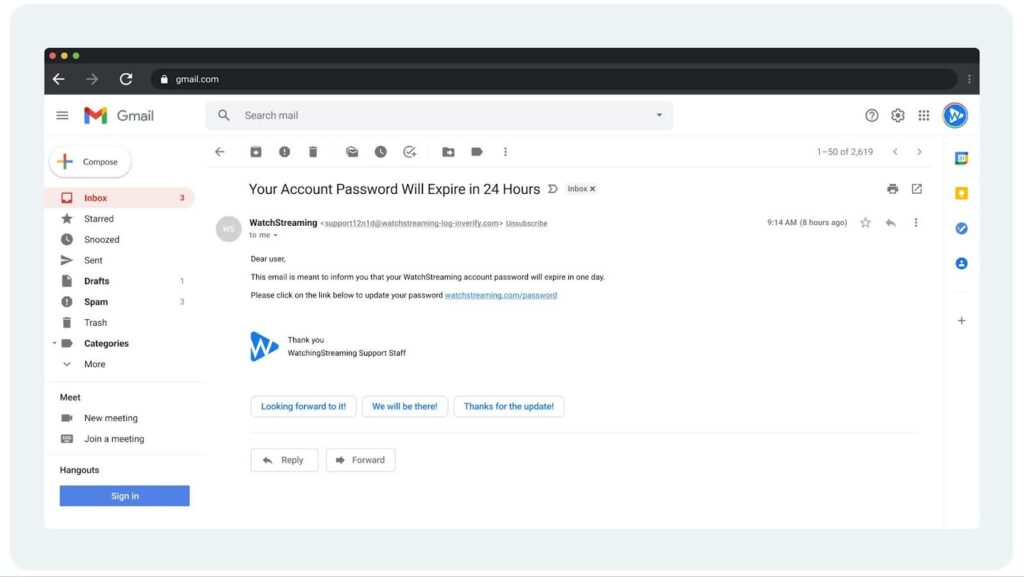
Recognizing the Red Flags
- Suspicious Profile: This scammer does a good job of appearing as a known contact — assuming the recipient uses the WatchStreaming platform. Many email phishing messages won’t have a profile name attached to it, or the email address will look like a jumble of letters. For example, the email address of “support12n1d@watchstreaming-log-inverify.com” is a red flag because it does not look like a real address. Plus, this scammer forgot to add a sender icon or image next to their name as part of their profile, which most legitimate companies include.
- Generic Greeting: The greeting is vague and impersonal. Nowadays, it’s incredibly easy for legitimate companies to set up dynamic greetings that include the recipient’s name. Generic phrases can mean something is off.
- Urgent Call to Action: The email creates a sense of urgency, pressuring the recipient to act quickly. Legitimate businesses will contact you well in advance of changes to your account or password expirations.
- Malicious Link: When an email has several suspicious elements, the inclusion of a link is a major concern. However, you can hover your cursor over the link to see the destination URL without actually clicking on it. If it is an unrecognizable URL, it’s a good indicator that the email is a scam. If you’re unsure, you can enter the URL into Google’s Safe Browsing search function to check.
Example 2: Phishing Text Messages (Smishing)
Phishing attacks are not just emails — they can also occur via both SMS and MMS text messages, known as “smishing.” Although email scams may be more prolific, phishing text messages may be more dangerous. Users seem to instinctively trust their phones more than their email. According to Textdip, text messages have a 98% open rate, roughly five times that of email. Plus, the click-through rate of text messages (that is, clicking on a link within a message) is between 19% and 35%. For email, it’s 1.86%.
See the text example below and the signs that it’s a scam.
Note: WatchStreaming is not a real company and is being used only as an example.
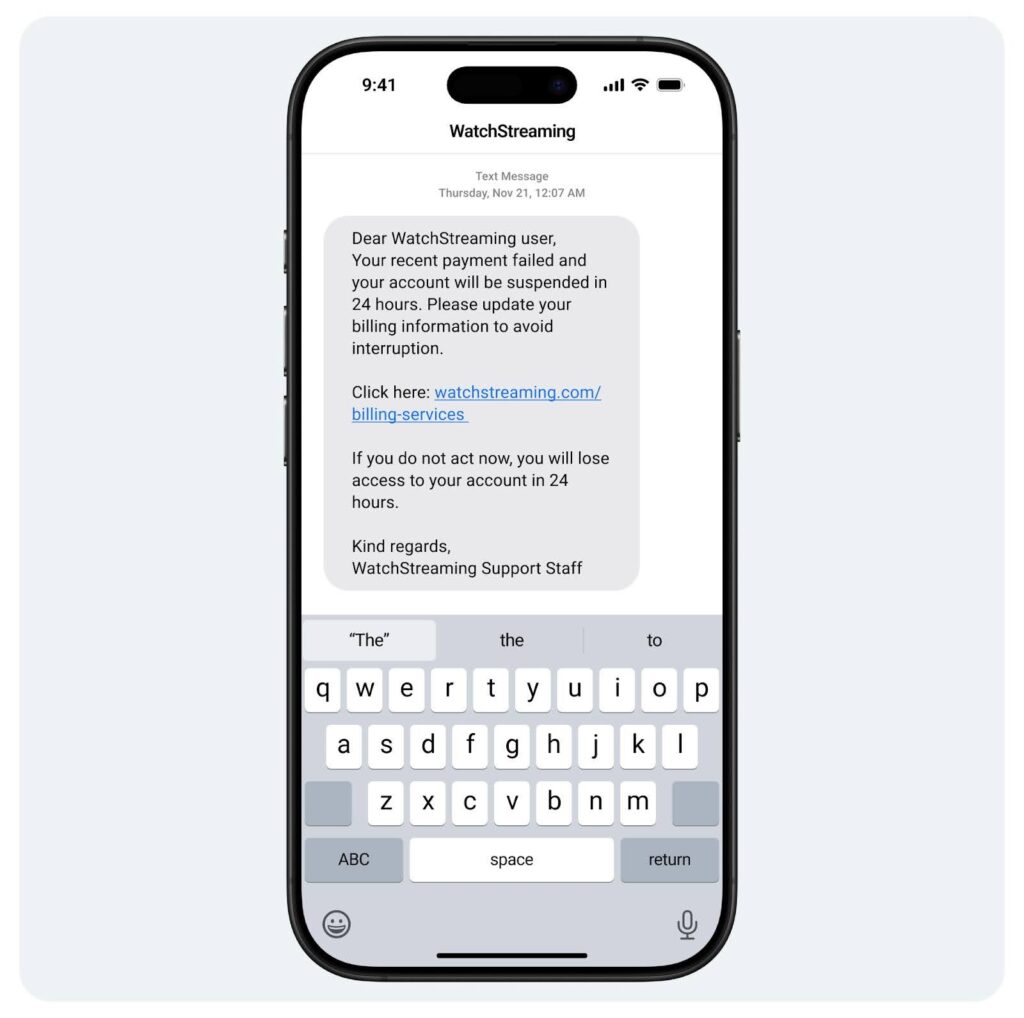
Recognizing the Red Flags
This phishing text message above has many of the same suspicious elements as the phishing email. However, here they take on a slightly different form and require special consideration:
- Unsolicited Message: This scammer is banking on the fact that you have a subscription to this streaming service. If you aren’t subscribed, you shouldn’t engage with the message. Even if you are subscribed, you should log in to your account separately from this message. If this notification is legitimate, it will appear there too.
- Suspicious Sender: While it’s unlikely that you’ll have streaming service support numbers saved in your phone, any message from an unknown number should be considered risky.
- Urgent Call to Action: This text message is trying to spark panic based on a narrow time limit. Remember, no company wants to make its customers feel uncomfortable. Such time crunches are simply unrealistic, especially for a first-time communication.
- Malicious Link: Whenever there’s a link, there’s a red flag. You won’t be able to hover over it like in the email example above, so try entering it into Google’s Safe Browsing search function.
Example 3: Phishing Phone Calls (Vishing)
Unfortunately, phishing isn’t just limited to text, links, and screens. Phishing attacks can also manifest as phone calls, a tactic known as “vishing.” While these are often robocalls or automated messages, which Americans tend to ignore or distrust anyway, you may also find yourself talking with a real person.
Below is a transcript of an example vishing scenario where a scammer calls a victim, posing as the support staff of a streaming service with the intention of getting the victim to verbally provide credit card information.
Note: WatchStreaming is not a real company and is being used only as an example.
Scammer: Hi, this is Jason from WatchStreaming customer support. Am I speaking with Rebecca?
Victim: Uh, yes, this is Rebecca. What’s this about?
Scammer: Thank you for confirming. I’m calling because we’ve detected an issue with your WatchStreaming account. It looks like your payment method failed when we tried to process your latest subscription renewal. If this isn’t resolved soon, your account may be deactivated, and we wouldn’t want that to happen!
Victim: Oh, really? That’s strange. I didn’t notice anything wrong.
Scammer: I completely understand — it often goes unnoticed. What likely happened is your credit card on file either expired or there was an issue with your bank. It’s an easy fix, though. I can help you get this sorted out in just a couple of minutes.
Victim: Okay, so what do I need to do?
Scammer: Great! First, can you confirm the billing address associated with your account? I want to make sure I’m speaking to the right person.
Victim: Uh, sure. It’s 1234 StreamSafely Road in Raleigh, North Carolina.
Scammer: Perfect! Alright, now all I need is for you to provide the credit card details you’d like to use to update the payment method on your account. If you could just give me the card number, expiration date, and the CVV code on the back of your card, we’ll have your subscription back on track right away.
Victim: Hang on, this doesn’t seem right. I don’t think companies ask for credit card information over the phone like this.
Scammer: Oh, no, no! I completely understand your concern. But don’t worry — this is our secure customer service line, and we’re just verifying the details to make sure your account stays active. If you don’t update the payment now, you could lose your access to WatchStreaming, and it may take several days to recover it.
Victim: I think I’ll just log in to my WatchStreaming account and check if there’s actually a problem. Thanks anyway. [Hangs up]
Recognizing the Red Flags
- Unsolicited Call: Unsolicited calls or “cold calling” is a common tactic scammers use. It’s safe to always be skeptical of any phone numbers you don’t recognize or calls you weren’t expecting.
- Pressure Tactics: The scammer creates a sense of urgency by claiming the account will be deactivated if the issue isn’t resolved immediately. This is a red flag.
- Requests for Sensitive Information: Legitimate companies rarely, if ever, ask for sensitive details like credit card information over the phone.
- Keeping the Victim On the Call: The scammer discourages the victim from hanging up or verifying the issue themselves. This is another common tactic.
How to Respond
It’s important to always refuse to share personal or financial information over the phone, and verify issues directly via the company’s official website or app.
In the scenario above, the victim does a great job of recognizing the signs, immediately ending the conversation, and going online to check their account for any signs of failed payment.
Example 4: Phishing via Payment Apps (Venmo, PayPal, Cash App Scams)
Phishing scams can also target payment apps, such as Venmo, PayPal, and Cash App. These scams may begin with a text or email notification, in which case the above rules apply. That said, let’s take a closer look at an example below.
Note: GoFunds Wallet is not a real company and is being used only as an example.
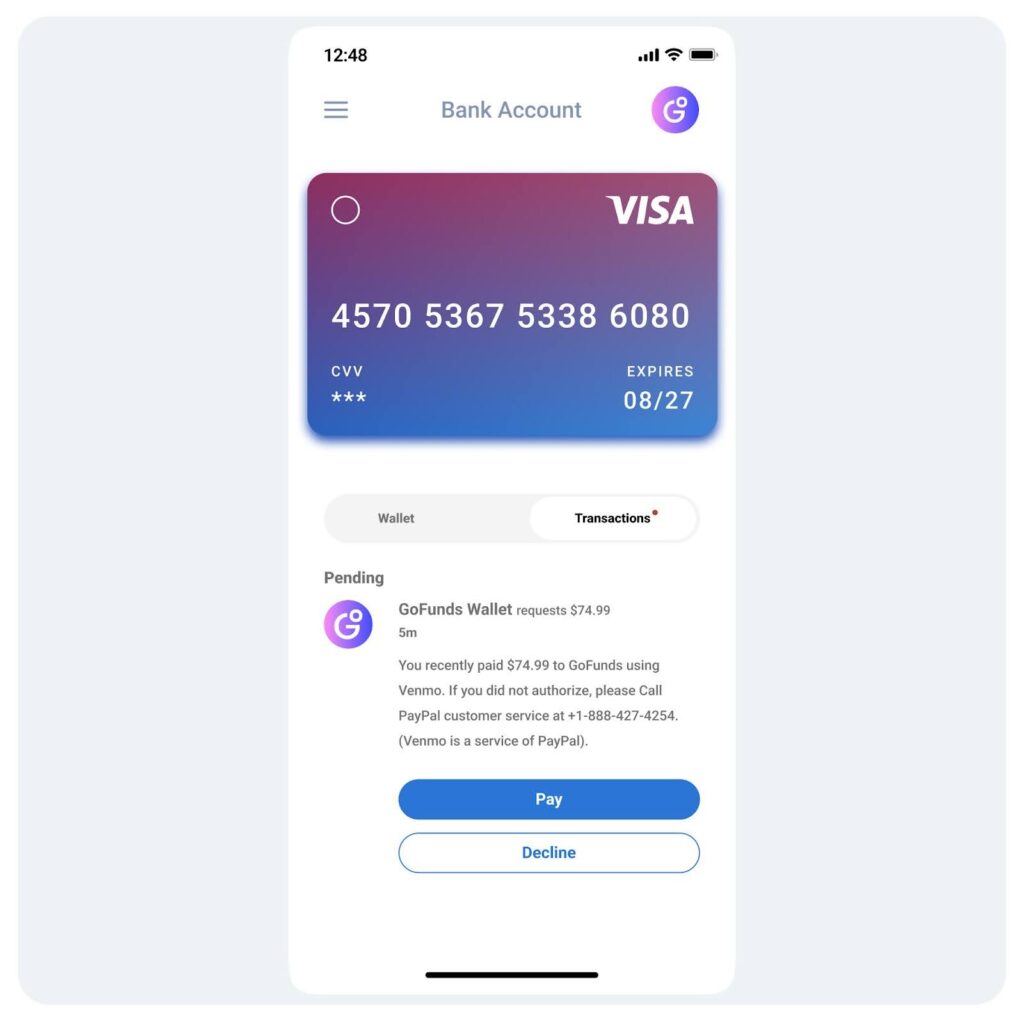
Recognizing the Red Flags
- Unsolicited Message: Whether the point of contact begins with an email, text, or in-app notification, recipients should always be wary of unsolicited communication and requests.
- Suspicious Sender: If you don’t use the payment service, seeing transactions from unfamiliar companies or companies that you simply do not use is an immediate red flag.
- Confirmation Request: This scammer tries to trick people by stating that the recipient already made a transaction and that it simply needs confirmation. This is meant to confuse people who make a lot of Venmo or PayPal transactions and lull them into a false sense of security. If you’re one of these individuals, always keep close track of your transactions and familiarize yourself with the companies you purchase from so that no suspicious activity flies under the radar. More importantly, payment confirmations are made during the sale. There is no reason that legitimate companies would have to send a follow-up confirmation after the fact.
- Poor Grammar: Scammers are not always based in the U.S., and their English may not be perfect. Any poor capitalization or missed punctuation in a message is a clear indicator that it did not come from a legitimate source.
Major Red Flags Across All Forms of Phishing
While the specific characteristics may vary, there are several common red flags that are seen across all types of phishing scams:
- Unsolicited Messages: If you did not initiate the communication or request the service or information, it’s likely a phishing attempt.
- Suspicious Sender: If you do not immediately recognize the sender or they do not have a sender icon, profile pic, or logo, be incredibly cautious.
- Generic Greetings: Remember, there’s no reason for companies that you work with to not know who you are. Phishing attempts often use generic greetings like “Dear Customer” instead of addressing the recipient by name.
- Urgency and Panicked Messaging: Remember, legitimate companies value customer service and try to work with their clients to come to a satisfactory resolution. Scammers, on the other hand, often create a sense of urgency or panic to pressure you into taking immediate action.
- Requests for Personal or Financial Information: Legitimate organizations will never ask for sensitive information like login credentials, social security numbers, or credit card information over unsolicited communications. Only provide such information to known, trusted organizations that you reach out to directly.
- Suspicious URLs and Links: Unsolicited communication that includes links or CTA buttons makes the situation exponentially more dangerous. Verify the destination URL when you can, but never click them.
If you have any doubts about the legitimacy of an email, text, phone call, or in-app notification, reach out to the sender in question yourself through another channel. Never go through the email or communication they provide. You can report phishing campaigns directly to the Federal Trade Commission and/or the FBI’s Internet Crime Complaint Center.
Find More Resources To Protect Yourself With StreamSafely
To learn more about phishing, digital piracy, and how scammers lure in consumers, we invite you to explore our library of online resources. We are dedicated to online security and the fight against piracy.
By teaming up with us, you can arm yourself with the knowledge and confidence to protect yourself from becoming a victim of phishing or other malicious schemes. Stay vigilant, and stream safely!





